EIGRP Questions 2
Question 1
What is the function of an EIGRP sequence TLV packet?
A. to acknowledge a set of sequence numbers during the startup update process
B. to list the peers that should listen to the next multicast packet during the reliable multicast process
C. to list the peers that should not listen to the next multicast packet during the reliable multicast process
D. to define the initial sequence number when bringing up a new peer
B. to list the peers that should listen to the next multicast packet during the reliable multicast process
C. to list the peers that should not listen to the next multicast packet during the reliable multicast process
D. to define the initial sequence number when bringing up a new peer
Answer: C
Explanation
EIGRP sends updates and other information between routers using multicast packets to 224.0.0.10. For example in the topology below, R1 made a change in the topology and it needs to send updates to R2 & R3. It sends multicast packets to EIGRP multicast address 224.0.0.10. Both R2 & R3 can receive the updates and acknowledge back to R1 using unicast. Simple, right?
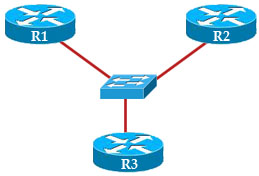
But what if R1 sends out updates, only R2 replies but R3 never does? In the case a router sends out a multicast packet that must be reliable delivered (like in this case), an EIGRP process will wait until the RTO (retransmission timeout) period has passed before beginning a recovery action. This period is calculated from the SRTT (smooth round-trip time). After R1 sends out updates it will wait for this period to expire. Then it makes a list of all the neighbors from which it did not receive an Acknowledgement (ACK). Next it sends out a packet telling these routers stop listening to multicast until they are been notified that it is safe again. Finally the router will begin sending unicast packets with the information to the routers that didn’t answer, continuing until they are caught up. In our example the process will be like this:
1. R1 sends out updates to 224.0.0.10
2. R2 responds but R3 does not
3. R1 waits for the RTO period to expire
4. R1 then sends out an unreliable-multicast packet, called a sequence TLV (Type-Length-Value) packet, which tells R3 not to listen to multicast packets any more
5. R1 continues sending any other muticast traffic it has and delivering all traffic, using unicast to R3, until it acknowledges all the packets
6. Once R3 has caught up, R1 will send another sequence TLV, telling R3 to begin listening to multicast again.
2. R2 responds but R3 does not
3. R1 waits for the RTO period to expire
4. R1 then sends out an unreliable-multicast packet, called a sequence TLV (Type-Length-Value) packet, which tells R3 not to listen to multicast packets any more
5. R1 continues sending any other muticast traffic it has and delivering all traffic, using unicast to R3, until it acknowledges all the packets
6. Once R3 has caught up, R1 will send another sequence TLV, telling R3 to begin listening to multicast again.
The sequence TLV packet contains a list of the nodes that should not listen to multicast packets while the recovery takes place. But notice that the TLV packet in step 6 does not contain any nodes in the list.
Note: In the case R3 still does not reply in step 4, R1 will attempt to retransmit the unicast 16 times or continue to retransmit until the hold time for the neighbor in question expires. After this time, R1 will declare a retransmission limit exceeded error and will reset the neighbor.
(Reference: EIGRP for IP: Basic Operation and Configuration)
Question 2
EIGRP allows configuration of multiple MD5 keys for packet authentication to support easy rollover from an old key to a new key. Which two statements are true regarding the usage of multiple authentication keys? (Choose two)
A. Received packets are authenticated by the key with the smallest key ID.
B. Sent packets are authenticated by all valid keys, which means that each packet is replicated as many times as the number of existing valid keys.
C. Received packets are authenticated by any valid key that is chosen.
D. Sent packets are authenticated by the key with the smallest key ID.
B. Sent packets are authenticated by all valid keys, which means that each packet is replicated as many times as the number of existing valid keys.
C. Received packets are authenticated by any valid key that is chosen.
D. Sent packets are authenticated by the key with the smallest key ID.
Answer: C D
Explanation
Suppose two routers are connected with each other via Fa0/0 interfaces and they are configured to authenticate via MD5. Below is a simple configuration on both routers so that they will work:
Router1(config)#key chain KeyChainR1
Router1(config-keychain)#key 1 Router1(config-keychain-key)#key-string FirstKey Router1(config-keychain-key)#key 2 Router1(config-keychain-key)#key-string SecondKey
Router2(config)#key chain KeyChainR2
Router2(config-keychain)#key 1 Router2(config-keychain-key)#key-string FirstKey Router2(config-keychain-key)#key 2 Router2(config-keychain-key)#key-string SecondKey |
Apply these key chains to R1 & R2:
Router1(config)#interface fastEthernet 0/0
Router1(config-if)#ip authentication mode eigrp 1 md5 Router1(config-if)#ip authentication key-chain eigrp 1 KeyChainR1
Router2(config)#interface fastEthernet 0/0
Router2(config-if)#ip authentication mode eigrp 1 md5 Router2(config-if)#ip authentication key-chain eigrp 1 KeyChainR2 |
There are some rules to configure MD5 authentication with EIGRP:
+ The key chain names on two routers do not have to match (in this case the name “KeyChainR1″ & “KeyChainR2″ do not match)
+ The key number and key-string on the two potential neighbors must match (for example “key 1″ & “key-string FirstKey” must match on “key 1″ & “key-string FirstKey” of neighboring router)
+ The key number and key-string on the two potential neighbors must match (for example “key 1″ & “key-string FirstKey” must match on “key 1″ & “key-string FirstKey” of neighboring router)
Also some facts about MD5 authentication with EIGRP
+ When sending EIGRP messages the lowest valid key number is used -> D is correct.
+ When receving EIGRP messages all currently configured valid keys are verified but the lowest valid one will be used -> Although answer C does not totally mention like that but it is the most suitable answer because A and B are totally wrong.
+ When sending EIGRP messages the lowest valid key number is used -> D is correct.
+ When receving EIGRP messages all currently configured valid keys are verified but the lowest valid one will be used -> Although answer C does not totally mention like that but it is the most suitable answer because A and B are totally wrong.
Answer A is not correct because we need valid key to authenticate.
As mentioned above, although answer C is not totally correct but it puts some light on why answer B is not correct: each packet is NOT “replicated as many times as the number of existing valid keys”. All currently configured valid keys are verified but the lowest valid one will be used.
Note: There are some books saying that the key numbers DO NOT have to match but if you have time please do a lab to verify that both key numbers and key-strings must match.
Question 3
Refer to the exhibit.

| R1: interface Loopback0 ip address 1.1.1.1 255.255.255.0 ipv6 address 2001:12::1/128 ipv6 eigrp 100 ! interface FastEthernet0/0 ip address 10.1.12.1 255.255.255.0 duplex auto speed auto ipv6 address 2001:112::1/64 ipv6 eigrp 100 ! interface FastEthernet0/1 no ip address shutdown duplex auto speed auto ! ip forward-protocol nd ! no ip http server no ip http secure-server ! ipv6 router eigrp 100 no shutdown ! control-plane ! | R2: interface Loopback0 ip address 2.2.2.2 255.255.255.0 ipv6 address 2001:12::2/128 ipv6 eigrp 100 ! interface FastEthernet0/0 ip address 10.1.12.2 255.255.255.0 duplex auto speed auto ipv6 address 2001:112::2/64 ipv6 eigrp 100 ! interface FastEthernet0/1 no ip address shutdown duplex auto speed auto ! ip forward-protocol nd ! no ip http server no ip http secure-server ! ipv6 router eigrp 100 shutdown ! control-plane ! |
How many EIGRP routes will appear in the routing table of R2?
A. 0
B. 1
C. 2
D. 3
B. 1
C. 2
D. 3
Answer: A
Explanation
EIGRPv6 on R2 was shut down so there is no EIGRP routes on the routing table of R2. If we turn on EIGRPv6 on R2 (with “no shutdown” command) then we would see the prefix of the loopback interface of R1 in the routing table of R2.
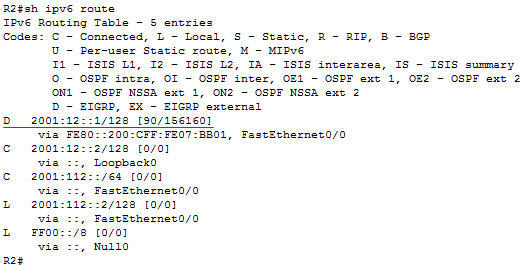
Note: EIGRPv6 requires the “ipv6 unicast-routing” global command to be turned on first or it will not work.
Question 4
In which type of EIGRP configuration is EIGRP IPv6 VRF-Lite available?
A. stub
B. named mode
C. classic mode
D. passive
B. named mode
C. classic mode
D. passive
Answer: B
Explanation
The EIGRP IPv6 VRF Lite feature provides EIGRP IPv6 support for multiple VRFs. EIGRP for IPv6 can operate in the context of a VRF. The EIGRP IPv6 VRF Lite feature provides separation between routing and forwarding, providing an additional level of security because no communication between devices belonging to different VRFs is allowed unless it is explicitly configured. The EIGRP IPv6 VRF Lite feature simplifies the management and troubleshooting of traffic belonging to a specific VRF.
The EIGRP IPv6 VRF Lite feature is available only in EIGRP named configurations.
Sign up here with your email

ConversionConversion EmoticonEmoticon