Question 1
What are the minimal configuration steps that are required to configure EIGRP HMAC-SHA2 authentication?
A. classic router mode, interface XX, authentication mode hmac-sha-256
Answer: C
Explanation
The example below shows how to configure EIGRP HMAC-SHA2 on Cisco router:
Device(config)# router eigrp name1
Device(config-router)# address-family ipv4 autonomous-system 45000
Device(config-router-af)# af-interface ethernet 0/0
Device(config-router-af-interface)# authentication mode hmac-sha-256 0 password1
Device(config-router-af-interface)# end
Device(config-router)# address-family ipv4 autonomous-system 45000
Device(config-router-af)# af-interface ethernet 0/0
Device(config-router-af-interface)# authentication mode hmac-sha-256 0 password1
Device(config-router-af-interface)# end
Question 2
What are two reasons to define static peers in EIGRP? (Choose two)
A. Security requirements do not allow dynamic learning of neighbors.
B. The link between peers requires multicast packets.
C. Back-level peers require static definition for successful connection.
D. The link between peers requires unicast packets.
B. The link between peers requires multicast packets.
C. Back-level peers require static definition for successful connection.
D. The link between peers requires unicast packets.
Answer: A D
Explanation
There are two ways we can create EIGRP neighbor relationship:
+ Use “network” command: this is the more popular way to create EIGRP neighbor relationship. That router will check which interfaces whose IP addresses belong to the and turn EIGRP on that interface. EIGRP messages are sent via multicast packets.
+ Use “neighbor” command: The interface(s) that have this command applied no longer send or receive EIGRP multicast packets. EIGRP messages are sent via unicast. The router only accepts EIGRP packets from peers that are explicitly configured with a neighbor statement. Consequently, any messages coming from routers without a corresponding neighbor statement are discarded. This helps prevent the insertion of unauthorized routing peers -> A and D are correct.
+ Use “network
+ Use “neighbor” command: The interface(s) that have this command applied no longer send or receive EIGRP multicast packets. EIGRP messages are sent via unicast. The router only accepts EIGRP packets from peers that are explicitly configured with a neighbor statement. Consequently, any messages coming from routers without a corresponding neighbor statement are discarded. This helps prevent the insertion of unauthorized routing peers -> A and D are correct.
Question 3
Which statement about the feasibility condition in EIGRP is true?
A. The prefix is reachable via an EIGRP peer that is in the routing domain of the router.
B. The EIGRP peer that advertises the prefix to the router has multiple paths to the destination.
C. The EIGRP peer that advertises the prefix to the router is closer to the destination than the router.
D. The EIGRP peer that advertises the prefix cannot be used as a next hop to reach the destination.
B. The EIGRP peer that advertises the prefix to the router has multiple paths to the destination.
C. The EIGRP peer that advertises the prefix to the router is closer to the destination than the router.
D. The EIGRP peer that advertises the prefix cannot be used as a next hop to reach the destination.
Answer: C
Explanation
The advertised metric from an EIGRP neighbor (peer) to the local router is called Advertised Distance (or reported distance) while the metric from the local router to that network is called Feasible Distance. For example, R1 advertises network 10.10.10.0/24 with a metric of 20 to R2. For R2, this is the advertised distance. R2 calculates the feasible distance by adding the metric from the advertised router (R1) to itself. So in this case the feasible distance to network 10.10.10.0/24 is 20 + 50 = 70.
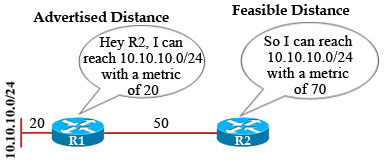
Before a router can be considered a feasible successor, it must pass the feasibility condition rule. In short, the feasibility condition says that if we learn about a prefix from a neighbor, the advertised distance from that neighbor to the destination must be lower than our feasible distance to that same destination.
Therefore we see the Advertised Distance always smaller than the Feasible Distance to satisfy the feasibility condition.
Question 4
How does EIGRP derive the metric for manual summary routes?
A. It uses the best composite metric of any component route in the topology table.
B. It uses the worst composite metric of any component route in the topology table.
C. It uses the best metric vectors of all component routes in the topology table.
D. It uses the worst metric vectors of all component routes in the topology table.
B. It uses the worst composite metric of any component route in the topology table.
C. It uses the best metric vectors of all component routes in the topology table.
D. It uses the worst metric vectors of all component routes in the topology table.
Answer: A
Explanation
For example if your router has a routing table like this:
| D 192.168.8.0/24 [90/2632528] via 192.168.0.1, 00:00:12, Serial0/0 D 192.168.9.0/24 [90/2323456] via 192.168.0.1, 00:00:12, Serial0/0 D 192.168.10.0/24 [90/2195456] via 192.168.0.1, 00:00:12, Serial0/0 D 192.168.11.0/24 [90/2323456] via 192.168.0.1, 00:00:12, Serial0/0 |
Now suppose you want to manually summarize all the routes above, you can use this command (on the router that advertised these routes to our router):
| Router(config-if)#ip summary-address eigrp 1 192.168.8.0 255.255.248.0 |
After that the routing table of your router will look like this:
| D 192.168.8.0/21 [90/2195456] via 192.168.0.1, 00:01:42, Serial0/0 |
And we can see the manual summary route takes the smallest metric of the specific routes.
Question 5
Refer to the exhibit.
You have configured two routing protocols across this point-to-point link. How many BFD sessions will be established across this link?
A. three per interface
B. one per multicast address
C. one per routing protocol
D. one per interface
B. one per multicast address
C. one per routing protocol
D. one per interface
Answer: D
Explanation
Cisco devices will use one Bidirectional Forwarding Detection (BFD) session for multiple client protocols in the Cisco implementation of BFD for Cisco IOS Releases 12.2(18)SXE, 12.0(31)S, and 12.4(4)T. For example, if a network is running OSPF and EIGRP across the same link to the same peer, only one BFD session will be established, and BFD will share session information with both routing protocols.
Question 6
Which two configuration changes should be made on the OTP interface of an EIGRP OTP route reflector? (Choose two)
A. passive-interface
B. no split-horizon
C. no next-hop-self
D. hello-interval 60, hold-time 180
B. no split-horizon
C. no next-hop-self
D. hello-interval 60, hold-time 180
Answer: B C
Explanation
The EIGRP Over the Top feature enables a single end-to-end Enhanced Interior Gateway Routing Protocol (EIGRP) routing domain that is transparent to the underlying public or private WAN transport that is used for connecting disparate EIGRP customer sites. When an enterprise extends its connectivity across multiple sites through a private or a public WAN connection, the service provider mandates that the enterprise use an additional routing protocol, typically the Border Gateway Protocol (BGP), over the WAN links to ensure end-to-end routing. The use of an additional protocol causes additional complexities for the enterprise, such as additional routing processes and sustained interaction between EIGRP and the routing protocol to ensure connectivity, for the enterprise. With the EIGRP Over the Top feature, routing is consolidated into a single protocol (EIGRP) across the WAN.
Perform this task to configure a customer edge (CE) device in a network to function as an EIGRP Route Reflector:
1. enable
2. configure terminal
3. router eigrp virtual-name
4. address-family ipv4 unicast autonomous-system as-number
5. af-interface interface-type interface-number
6. no next-hop-self
7. no split-horizon
8. exit
9. remote-neighbors source interface-type interface-number unicast-listen lisp-encap
10. network ip-address
11. end
2. configure terminal
3. router eigrp virtual-name
4. address-family ipv4 unicast autonomous-system as-number
5. af-interface interface-type interface-number
6. no next-hop-self
7. no split-horizon
8. exit
9. remote-neighbors source interface-type interface-number unicast-listen lisp-encap
10. network ip-address
11. end
Note: Use no next-hop-self to instructs EIGRP to use the received next hop and not the local outbound interface address as the next hop to be advertised to neighboring devices. If no next-hop-self is not configured, the data traffic will flow through the EIGRP Route Reflector.
Question 7
What is the purpose of EIGRP summary leaking?
A. to allow a summary to be advertised conditionally on specific criteria
B. to allow a component of a summary to be advertised in addition to the summary
C. to allow oveR1apping summaries to exist on a single interface
D. to modify the metric of the summary based on which components of the summary are operational
B. to allow a component of a summary to be advertised in addition to the summary
C. to allow oveR1apping summaries to exist on a single interface
D. to modify the metric of the summary based on which components of the summary are operational
Answer: B
Explanation
When you do manual summarization, and still you want to advertise some specific routes to the neighbor, you can do that using leak-map. Please read more about leaking routes here: http://www.cisco.com/c/en/us/td/docs/ios/iproute_eigrp/command/reference/ire_book/ire_i1.html#wp1037685.
Question 8
Which statement about the function of poison reverse in EIGRP is true?
A. It tells peers to remove paths that previously might have pointed to this router.
B. It tells peers to remove paths to save memory and bandwidth.
C. It provides reverse path information for multicast routing.
D. It tells peers that a prefix is no longer reachable.
B. It tells peers to remove paths to save memory and bandwidth.
C. It provides reverse path information for multicast routing.
D. It tells peers that a prefix is no longer reachable.
Answer: A
Explanation
Poison Reverse in EIGRP states: “Once you learn of a route through an interface, advertise it as unreachable back through that same interface”. For more information please read here: http://www.cisco.com/c/en/us/support/docs/ip/enhanced-interior-gateway-routing-protocol-eigrp/16406-eigrp-toc.html#splithorizon.
Question 9
What is the preferred method to improve neighbor loss detection in EIGRP?
A. EIGRP natively detects neighbor down immediately, and no additional feature or configuration is required.
B. BFD should be used on interfaces that support it for rapid neighbor loss detection.
C. Fast hellos (subsecond) are preferred for EIGRP, so that it learns rapidly through its own mechanisms.
D. Fast hellos (one-second hellos) are preferred for EIGRP, so that it learns rapidly through its own mechanisms.
B. BFD should be used on interfaces that support it for rapid neighbor loss detection.
C. Fast hellos (subsecond) are preferred for EIGRP, so that it learns rapidly through its own mechanisms.
D. Fast hellos (one-second hellos) are preferred for EIGRP, so that it learns rapidly through its own mechanisms.
Answer: B
Question 10
Which two statements about the function of the stub feature in EIGRP are true? (Choose two)
A. It stops the stub router from sending queries to peers.
B. It stops the hub router from sending queries to the stub router.
C. It stops the stub router from propagating dynamically learned EIGRP prefixes to the hub routers.
D. It stops the hub router from propagating dynamically learned EIGRP prefixes to the stub routers.
B. It stops the hub router from sending queries to the stub router.
C. It stops the stub router from propagating dynamically learned EIGRP prefixes to the hub routers.
D. It stops the hub router from propagating dynamically learned EIGRP prefixes to the stub routers.
Answer: B C
Sign up here with your email

ConversionConversion EmoticonEmoticon